Reading: OAuth 2
OAuth 2
The OAuth 2 spec can be a bit confusing to read, so I’ve written this post to help describe the terminology in a simplified format. The core spec leaves many decisions up to the implementer, often based on security tradeoffs of the implementation. Instead of describing all possible decisions that need to be made to successfully implement OAuth 2, this post makes decisions that are appropriate for most implementations.
Roles
The Third-Party Application: “Client” - The client is the application that is attempting to get access to the user’s account. It needs to get permission from the user before it can do so.
The API: “Resource Server” - The resource server is the API server used to access the user’s information.
The Authorization Server - This is the server that presents the interface where the user approves or denies the request. In smaller implementations, this may be the same server as the API server, but larger scale deployments will often build this as a separate component.
The User: “Resource Owner” - The resource owner is the person who is giving access to some portion of their account.
Authorization
The first step of OAuth 2 is to get authorization from the user. For browser-based or mobile apps, this is usually accomplished by displaying an interface provided by the service to the user.
OAuth 2 provides several “grant types” for different use cases. The grant types defined are: - Authorization Code for apps running on a web server, browser-based and mobile apps - Password for logging in with a username and password (only for first-party apps) - Client credentials for application access without a user present - Implicit was previously recommended for clients without a secret, but has been superseded by using the Authorization Code grant with PKCE.
Abstract Protocol Flow
Now that you have an idea of what the OAuth roles are, let’s look at a diagram of how they generally interact with each other:
- 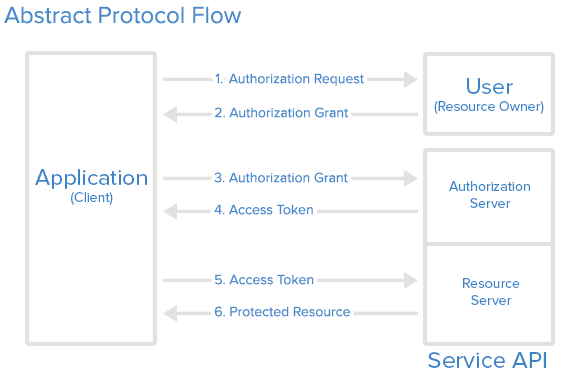
Here is a more detailed explanation of the steps in the diagram:
- The application requests authorization to access service resources from the user
- If the user authorized the request, the application receives an authorization grant
- The application requests an access token from the authorization server (API) by presenting authentication of its own identity, and the authorization grant
- If the application identity is authenticated and the authorization grant is valid, the authorization server (API) issues an access token to the application. Authorization is complete.
- The application requests the resource from the resource server (API) and presents the access token for authentication
- If the access token is valid, the resource server (API) serves the resource to the application

